The next time you post something on Facebook, LinkedIn, YouTube or practically anywhere else on the Internet, keep in mind you’re leaving cyber crumbs behind.
The trail can become key evidence in a lawsuit, as purported bigamist John France of Westlake learned when his wife discovered he had married someone new after she saw wedding photos of France and Wife 2 on Facebook a few years ago.
Granted, the photos weren’t exactly discreet. The wedding ceremony had been at Disney World in Orlando, Fla., with France dressed as Prince Charming and his new bride as Sleeping Beauty, surrounded by footmen.
While the France case may be over the top, gathering evidence from social media sites and other Internet sources has become quite routine in law practices. Family law, workers’ comp, trademark infringement and defamation litigation all lend themselves to sweeps of social media sites to bolster cases.
“The proverbial ‘smoking gun’ document of the pre-Internet era, which had given way to smoking gun email, has now given way to the smoking gun social media post,” attorneys Joshua Briones and Ana Tagvoryan write in “Social Media as Evidence,” newly published by the American Bar Association.
The authors point to the staggering growth of social media as tracked by pewinternet.org. Eighty percent of Americans who are online now regularly use some form of it. By the end of 2012, there were 200 million blogs worldwide, 901 million monthly active users of Facebook, more than 260 million users on Myspace, 160 million LinkedIn users, 340 million Tweets every 24 hours and 4 billion YouTube views per day, according to the Pew Research Center.
People will say things on social media sites that they would never say around the water cooler, said Tracy Johnson, an intellectual-property lawyer at Calfee Halter & Griswold in Cleveland.
“I think there’s a certain feeling of social anonymity,” Johnson said. “Also, I don’t think people really understand — certainly they don’t think about — the permanence of what they said or how they’re saying it. Sometimes it’s practically impossible to pull back an utterance online.”
An utterance or an image: Police in the recent conviction of Taunee Smith in the 2011 murder of DeJohn Dammons in Euclid used Facebook photos to identify Smith as present on the night of the shooting.
In an Arizona criminal case, prosecutors used the Myspace profile of Kirk Pressley Jr. to prove his Internet usage and alcohol consumption in violation of his probation. Pressley argued unsuccessfully on appeal that the trial court erred in admitting Myspace photographs.
On the civil side, litigants are checking social media sites as a standard part of due diligence for their clients. And insurance companies comb Facebook and Twitter accounts to assess the status of clients who file accident and personal injury claims.
Intellectual-property lawyer Philip Bautista at the Cleveland office of Taft, Stettinius & Hollister, said lawyers there make regular anti-piracy checks of social media sites. They’re looking for trademark and copyright infringements on clients with large portfolios of brands, including the Hershey Co. and gun manufacturer Heckler & Koch, he said.
“You can look at a business’s Facebook page and determine when an opposing party has used the trademark at issue,” Bautista said.
Briones and Tagvoryan say blogs and even the comments posted on them have deepening legal reach.
Court clerks use blogs as a source for researching legal issues, in the same way they used law review comments in the past, they said. U.S. Supreme Court Justice Anthony Kennedy recently remarked that comments on law review articles come out too late to be of use to the court, so he finds his clerks reading blogs for insight on cases pending before the court.
Internet sites are not culled only for evidence to prove cases or impeach witnesses. Online posting itself can be the subject of a lawsuit, as a South Carolina woman found when Med Express of Medina sued her over a complaint she wrote on eBay.
The posting by Amy Nicholls of Greenville, S.C., was not extremely critical. She said the microscope she bought from medical equipment supplier Med Express arrived with $1.44 in postage due. She posted that information online and gave the company a low rating on eBay’s feedback forum.
Med Express admitted its shipping error, offered to reimburse Nicholls for the postage and asked her to take down her posting. When Nicholls refused to retract it, Med Express responded with a defamation lawsuit.
“We certainly admit that it arrived postage due,” said Med Express lawyer James Amodio, who said the postage problem apparently arose because of a weighing error with the package.
Amodio said Med Express insisted on a retraction because the company sells exclusively over eBay, where a sufficient level of negative feedback can increase the cost of sales as well as possibly drive away customers.
A hearing in the case is set for May 2.
Paul Levy, staff attorney for the consumer advocacy group Public Citizen, blogged about the case in the hopes of finding a pro bono attorney for the defendant. Public Citizen itself usually doesn’t take on cases such as Nicholls’, at least at the trial court level.
“There are so many defamation cases out there, we couldn’t defend everyone,” Levy said, “and it would only scratch the surface.”
Gun advocates — some with rifles slung across shoulders or pistols holstered at the hip — have rallied peacefully in state capitals nationwide against President Barack Obama’s sweeping federal gun-control proposals.
Summoned via social media for the “Guns Across America” event, participants gathered Saturday for protests large and small against stricter limits sought on firearms. Only a few dozen turned out in South Dakota and a few hundred in Boise, Idaho. Some 2,000 turned out in New York and large crowds also rallied in Connecticut, Tennessee, Texas, Utah and Washington state.
The rallies came on a day in which accidental shootings at gun shows in North Carolina, Indiana and Ohio left five people hurt. The wounded included two bystanders hit by shotgun pellets after a 12-gauge shotgun discharged at a show in Raleigh, N.C., as the owner unzipped its case for a law officer to check at a security entrance, authorities said. A retired deputy there also suffered a slight hand injury.
About 800 people gathered for the “Guns Across America” event in Austin, Texas, as speakers took to the microphone under a giant Texas flag stamped with one word: “Independent.”
“The thing that so angers me, and I think so angers you, is that this president is using children as a human shield to advance a very liberal agenda that will do nothing to protect them,” said state Rep. Steve Toth, referencing last month’s elementary school massacre in Newtown, Conn.
Obama recently announced the gun-control proposals in the wake of a Connecticut elementary school shooting that killed 20 first-graders and six educators last month.
Toth, a first-term Republican lawmaker from The Woodlands outside Houston, has introduced legislation to ban within Texas any future federal limits on assault weapons or high-capacity magazines, though such a measure would violate the U.S. Constitution.
In Arizona, Oregon and Utah, some came with holstered handguns or rifles on their backs.
One man in Phoenix dressed as a Revolutionary War Minuteman, completing his outfit with an antique long rifle and a sign reading: “Tyrants Beware – 1776.”
“We’re out here because this country has some very wise founding fathers and they knew they were being oppressed when they were a British colony,” said another man at the Phoenix rally, Eric Cashman. “Had they not had their firearms … to stand up against the British, we’d still be a British colony.”
Rallies at statehouses nationwide were organized by Eric Reed, an airline captain from the Houston area who in November started a group called “More Gun Control (equals) More Crime.” Its Facebook page has been “liked” by more than 17,000 people.
At the New York state Capitol in Albany, about 2,000 people turned out for a chilly rally, where they chanted “We the People,” ”USA,” and “Freedom.” Many carried American flags and “Don’t Tread On Me” banners. The event took place four days after Democratic Gov. Andrew Cuomo signed the nation’s toughest assault weapon and magazine restrictions.
In Connecticut, where task forces created by the Legislature and Democratic Gov. Dannel Malloy are considering changes to gun laws, police said about 1,000 people showed up on the Capitol grounds. One demonstrator at the rally in Maine, Joe Getchell of Pittsfield, said every law-abiding citizen has a right to bear arms.
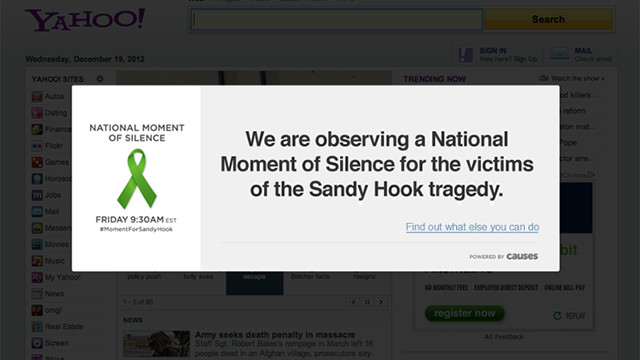 Some major websites will go dark for one minute Friday at 9:30 a.m. ET as part of a national moment of silence for the victims of last week’s shooting at Sandy Hook Elementary School in Newtown, Connecticut.
Some major websites will go dark for one minute Friday at 9:30 a.m. ET as part of a national moment of silence for the victims of last week’s shooting at Sandy Hook Elementary School in Newtown, Connecticut.
It’s unclear how widespread participation will be online, but more than 100,000 people and sites have pledged to participate on the Causes.com page for the Web Goes Silent campaign. People and companies are also spreading the word by tweeting their intention to go quiet with the hashtag #momentforSandyHook.
High-profile Silicon Valley venture capitalist Ron Conway is working hard to promote the online moment of silence, which is part of a larger campaign for federal gun control legislation. Conway is leading the Causes.com campaign along with other big names including Ryan Seacrest, Jack Dorsey, Britney Spears, MC Hammer, Suze Orman and Tyler Florence.
Causes.com is a startup that uses social media to raise awareness and funds for charities and causes. Conway is also an investor in the for-profit company.
Any site that wants to participate in Friday’s moment of silence can do so on its own, or it can embed an official badge with a green ribbon on its site. At webmomentofsilence.org, companies can sign up to receive a bit of JavaScript that will make the process easier. Sites using the code will appear grayed out in the background with a white box in the foreground that reads “We are observing a National Moment of Silence for the victims of the Sandy Hook tragedy.”
Conway joined other tech notables and some celebrities to demand action for stronger gun control in a full-page ad in the Wednesday print edition of the New York Times. The ad was run by Mayors Against Illegal Guns, a lobbying group of more than 700 U.S. mayors. It started the Demand A Plan campaign to reform gun laws after the Aurora, Colorado, shootings in July, and it has seen a surge in new support after the Sandy Hook shootings.
This is not the first time major sites have banded together to go dark for a cause. This year, major tech names staged an immense and successful online protest against the Stop Online Privacy Act.
 The world of legal support is evolving around us much faster than most of us anticipated and were prepared to address. Technology waits for no one and pushes forward constantly, shrinking the world and putting everything right at our fingertips. It is so very crucial now to ride the crest of that wave and not get left behind. The days of old school service of process have given way to the demands of the legal practice embracing current new technologies, thereby raising their expectations of what legal support professional provide and how quickly they can deliver. It is so crucial that we, as a whole, embrace this trend and engage fully in the art of staying current and relevant. The following are some suggestions that can be useful to that end.
The world of legal support is evolving around us much faster than most of us anticipated and were prepared to address. Technology waits for no one and pushes forward constantly, shrinking the world and putting everything right at our fingertips. It is so very crucial now to ride the crest of that wave and not get left behind. The days of old school service of process have given way to the demands of the legal practice embracing current new technologies, thereby raising their expectations of what legal support professional provide and how quickly they can deliver. It is so crucial that we, as a whole, embrace this trend and engage fully in the art of staying current and relevant. The following are some suggestions that can be useful to that end.
1. Educate yourself
-Attend professional workshops, seminars and Legal Tech conferences
-Read, learn and understand the codes that affect our profession
-Understand the trend within law offices to meet their evolving needs
2. Join and/or Sponsor Local, State and National Associations
-Process Serving, Photocopy, Investigation and Collections Associations
-Secretary, Paralegal or Legal Professional/Assistant and Bar Associations
-Chambers of Commerce, Business Groups and Service Organizations
-Sheriff, Marshall and Constable Associations
3. Join Topical User Groups, Newsgroups, and Stay Current with Discussions
-Observe trends and use foresight to predict likely directional shifts
-Identify top commentators and follow their posts
4. Join Job Listing and Job Posting Sites
-Ask for additional information to give an accurate quote
-Respond quickly with details of what you will provide
5. Make a Commitment to Educate Your Staff and Contractors
-Encourage or require participation in training programs and events
-Bring in educators and experts to provide in-house training
-Take advantage of online educational opportunities
6. Sign Up for Public Notices from the State and Federal Courts in your Area
-Be among the first in your area to receive alerts and info blasts
-Forward relevant information in a newsletter or e-blasts to your clients
7. Read and Follow Professional Publication, Trade Magazines, Newsletters and E-zines
-Example: CALSPro Press (CA), The Docket Sheet (National)
-The Serve Report
8. Use Social Media and Locate Blogs that Keep you Informed
-Check in daily to stay current
-If available, sign up for auto-notification when new content is released
9. Follow Proposed Legislation and Legislative Digests on Matters of Potential Concern
-Track State and National Bills potentially impacting service of process
-Digest and fully understand all related legislative changes and how they affect you
10. Educate Your Clients and Customers
-Host trainings for your customers at your location or theirs
-Forward upcoming MCLE opportunities as a service to your clients
11. Get Active and Participate at a Higher Level in Associations and other Professional Groups
-Submit articles and/or posts, and weigh in on current topics
-Become a committee member or even chair a committee
-Run for an elected office or seek appointment and help shape our future
12. Embrace Changing Technologies, Keep your Website Fresh and Lively, and Improve Your Timelines and Methods of Delivering Information to Your Clients and Customers
These suggestions are only some basic ideas to be a springboard for your ongoing effort to position yourself or your company in a way to remain ever relevant. By continuing to keep this concept at the forefront of your thoughts and business plan, you will in fact be engaged in the evolutionary process and may even become an agent for what legal support will become in the years ahead.
People use their computers and tablets. Who’s tracking you online?
1. Read the agreements for all mobile phone apps before you download them. Some of them are scary! They will track your location using your GPS and some (like Facebook) will download ALL OF THE CONTACTS IN YOUR PHONE. Can’t remember who you’ve handed your data to? MyPermissions can help.
2. Read the Terms of Service Agreements for sites you give your information to. Especially sites you give your financial information to. You maybe thinking:”I’ve been on page 5 of Freedom for 8 months, HOW am I going to find the time to read online agreements?” ToS;DR can help.
3. Use a search engine that doesn’t track you, like DuckDuckGo or Startpage for searches you want to keep private. Google’s Incognito setting, Microsoft’s Do Not Track setting and other browser privacy settings are not always effective, because they typically leave the decision of whether to track you up to the website you visit. There are no regulations requiring websites honor a “Do Not Track” request.
4. Use a browser add-on like Ghostery, Privacyfix or Do Not Track Plus to see who is tracking you on any given website. You can use these tools to avoid being tracked altogether or to limit who can access your data.
5. Use a tool to encrypt your connection, like CyberGhost VPN or Tor (which routes your search through servers all over the globe, the way criminals in the movies route their calls to avoid having them traced). Be sure to use one of these tools if you are accessing the Internet through a public WiFi connection at a coffee shop, for instance.
6. Adjust your Facebook privacy settings so that only your friends can see your information. You know that 6 Degress of Kevin Bacon game? That should give you an idea of how many friends your friends have and how many thousands of people can see your information (not to mention the impressive scope of Bacon’s work)
7. Have different email addresses for different things, i.e. an email for work, a personal email, and an email you give to online stores. This makes it harder for companies to flesh out a profile of you. You can also use an email cloaking device like Gliph.
8. Use different passwords for different sites. A lot of sites store your password and know your email login name. You may be thinking that there is no way you will be able to remember any password more complicated than “Password,” but take heart! LastPass can help you with that.
9. Regularly clear out the cookies and caches in your computer. Many companies will track you for months if you don’t clean these out. Cookies aren’t the only way companies track you, but it will help. This site can be used to clean up your cache.
10. Use a service that removes your data from data brokers, like DeleteMe, Safe Shepherd and Catalog Choice. They usually charge a monthly fee and they won’t remove your online profile entirely, but it will help.
 In light of the massive Twitter security breach (yes, we’re still skeptical of the claim that it was just a password reset) earlier this month, some users might be worried about protecting their accounts on social media networks.
In light of the massive Twitter security breach (yes, we’re still skeptical of the claim that it was just a password reset) earlier this month, some users might be worried about protecting their accounts on social media networks.
Andrew Jaquith, CTO of Perimeter E-Security and former Forrester analyst on password security, posted some great suggestions regarding account security on the Perimeter E-Security blog (where he is a frequent contributor). Consider this one a freebie, social network aficionados! It’s not every day you get expert advice at no charge.
Protip no. 1: Password expiration:
“Prevailing security dogma holds that security passwords should be complex and frequently changed. But requiring your employees to change their passwords every 90 days just annoys them, and they will do highly insecure things to cope as a result. They will scribble passwords on sticky notes, re-use the same password everywhere, or make the absolute smallest changes to their passwords that they can while still complying with policy.
“For example, an employee might pick a ‘complex’ 8-character password ‘rosebud1!’ and then increment the ’1′ every 90 days. Even worse, because passwords must be changed so often, IT managers use the shortest passwords their regulators will let them squeak buy with: 8 characters.
“For these reasons, researchers from Microsoft, Cambridge University among other institutions have concluded that password aging is a massive waste of time.
“It’s far better to require comparatively longer passwords that never change, such as passphrases or mnemonic passwords. Although employees will face a slightly longer learning curve initially, once they commit them to memory, they becomes reflexes. The best part: long passphrases can’t be broken as easily, so you’ve increased security and productivity at the same time.“
Protip no. 2: Using LDAP, AD, and single sign-onto reduce passwords you need to remember:
“As with password length and aging considerations, the employee’s ability to remember their passwords is a strong predictor of how likely (or unlikely) they will be to behave in ways that are less secure. The fewer passwords they have to remember, the less likely they are to make mistakes or game the system.
“Tying your applications into your LDAP or Active Directory servers is a good way to reduce the burden — think of it as the poor-man’s SSO. Full-blown single-sign-on (SSO) systems, of course, are even better. Consolidating password stores has benefits beyond just convenience, though.
“You also get better security because you can centrally enforce your password policies, and suspend access to applications and infrastructure much more quickly.”
 Social media is here to stay – in the living room, at the kitchen table, at the movies, in the coffee shop, and even in the workplace. The boom of mobile applications has taken popular social web apps like Facebook, Twitter, Pinterest, and LinkedIn to new levels of user growth and virality. More users mean more data; and where there is data, you’re likely to find a case for electronic discovery (or e-discovery, for short).
Social media is here to stay – in the living room, at the kitchen table, at the movies, in the coffee shop, and even in the workplace. The boom of mobile applications has taken popular social web apps like Facebook, Twitter, Pinterest, and LinkedIn to new levels of user growth and virality. More users mean more data; and where there is data, you’re likely to find a case for electronic discovery (or e-discovery, for short).
Let’s start with a definition. Electronic discovery is the process of searching for and finding electronically stored information (ESI) – often a procedural necessity in civil litigation. In the past, we’ve thought about e-discovery when dealing with such things as the exchange of company email, saved documents, etc.. If any of these things were evidentiary in nature, they might be “discovered,” (using some form of software for e-discovery) and presented as evidence in court proceedings.
Social media, as it happens, is no different. I alluded earlier to the fact that employee-to-employee communication via social media during the workday has become no less than a commonality. In some companies, it’s actually encouraged. Many executives contend that social media use can in fact improve overall productivity. While this sort of encouragement is obviously warranted (to some degree), it should not come without preparedness for possible litigation down the road.
Collecting Social Media Data
This is the ‘how’ side of the coin. It is imperative that – before moving forward with encouraging workplace social media communication – you understand how you’re going to collect social media data. Social media is sort of the Wild West of the Web. Communications are moving so quickly in such high volumes that it’s hard to keep track of the goings on. Unfortunately, “it’s too hard” won’t get you any slack cut in a court of law.
For this reason, it’s a good idea to explore all of the possible options for collecting social media data. Some of the avenues you might explore include:
-Screen shots of communications
-Communications sent/monitored via proxy server
-Communications indexed by custom web crawler
-Communication data pulled from application APIs
There are other viable solutions worth considering. As is the case with those listed above, each method will always have its pros and cons. Nonetheless, it’s vital that you have some methodology in place before you give the go-ahead.
Implementing Defensible Policies
To be discovered, the data must first exist. One of the key aspects of surviving an e-discovery request is the presence of defined retention and litigation hold policies. This is true of document discovery, as well as email. You can bet that it’s true of social media e-discovery.
With a retention policy, companies can provide a stringent outline of the type of social media data they collect, where they archive it, and how long they keep it archived. This way, when the deletion of a particular item comes up in litigation, there are clear guidelines that point to the defensibility (or lack thereof) of the deletion. The system understands that storage is an issue; data won’t be stored forever.
A litigation hold policy, on the other hand, is put into effect when a company suspects impending litigation. The primary function of this policy is to mandate that any data that might be evidentiary in nature remains archived (and undeleted). With social media, though, the litigation hold policy might include limitations on future social media communications (Facebook posts, Twitter tweets, Pinterest pins, etc.), changes in the types of communications permitted during the period prior to litigation, etc. Any and all of these things are worth considering. With email, a comprehensive litigation support software can aid you in implementing these policies.
Social media is a great tool. It can breed collaborative culture and even productivity in the workplace. However, without strict policies in place to govern social media communications and methodologies to collect and archive those communications, it will be difficult to build a legitimate defense when workplace social media exchanges become the subject of litigation. Prepare your strategy early, and you’ll be able to relax down the road.
![]() Do You Have a 4th Amendment Privacy Right Over Your Public Postings?
Do You Have a 4th Amendment Privacy Right Over Your Public Postings?
Once you publicly display your images or thoughts on public forums, they are no longer your private property. If you have a run in with the law, the court may use this information against you. And rest assured that the prosecuting attorney charging you will find a way to subpoena those tweets and images.
Twitter Submits Subpoenaed Tweets to Judge
A Wall Street protester named Malcolm Harris was arrested and faced criminal charges for disregarding police orders during the Wall Street protest at the Brooklyn Bridge. Apparently, the protestors were told not to cross the bridge. During the protests Harris apparently tweeted information relevant to his was awareness of these police orders. Judge Matthew A. Sciarrino Jr., who is overseeing his criminal trial, wanted access to these tweets. Harris argued that his tweets are private property and cannot be made available to the court. However, the Judge opined that Twitter users do not own their tweets and Twitter should hand them over when subpoenaed. His tweets for the period of September 15, 2011 to December 31, 2011 were eventually submitted to the Judge. Of course, Harris was not too happy when Twitter handed over his private information to the Judge.
Unfortunately, it seems as though neither Harris nor any of us have Fourth Amendment privacy protection when it comes to our social networking accounts.
Consequences of Posting Photos or Thoughts on Social Networking Sites
The next time you think about posting an inappropriate photo, or tweeting about how much you like to party with your “bros” in Las Vegas, sleep on it before posting it. You never know how it will effect your rights at let’s say, your child custody hearing.
 The widespread adoption of YouTube has proven to be an invaluable vehicle for police departments, who are posting video surveillance footage on YouTube to gain traction in solving crimes.
The widespread adoption of YouTube has proven to be an invaluable vehicle for police departments, who are posting video surveillance footage on YouTube to gain traction in solving crimes.
The reason is in the YouTube user statistics themselves: More than 800 million unique users visit YouTube each month; more than three billion hours of video are viewed per month, with more than one trillion hours viewed in 2011; nearly 100 million people take social action after viewing a video every week.
There are nearly 40 police departments posting surveillance video on YouTube, including Kansas City, Philadelphia, Detroit, Baltimore, Houston, Tucson, Milwaukee, Portland, and Minneapolis.
The Milwaukee Police Department is a use-case for this growing law enforcement trend. The department has harnessed YouTube as an outreach tool since 2008; and since that time, the department has also become entrenched in the social media realm. Milwaukee’s Police Department has generated an impressive following on Facebook and Twitter, and sees these channels as a way to create an ongoing dialogue with the public.
“It’s been very positive,” Anne Schwartz, director of communications at the Milwaukee Police Department, says of YouTube’s impact on her department. “Someone can watch a video on our website or on YouTube and read the entire description and pause it if they want to, and really take a good look at it. We’ve solved crimes that way. We’ve had people that see these videos, and then recognize the suspect in that video.”
The Philadelphia Police Department created a YouTube channel in May 2008, a month after Milwaukee did. The department shares videos of unsolved crimes from each police division, ranging from burglaries and robberies to assaults and abductions, which, as a whole, have had more than 1.8 million views. “We’ve released just over 250 videos on YouTube and now have around 90 arrests,” said PPD Social Media Community Manager Frank Domizio.
To protect the privacy of anyone who divulges information on a crime, comments are disabled on every video posted by the two police departments. Users are provided with a phone number and email to contact the police divisions if they know something or recognize someone. To avoid legal troubles, the faces of bystanders are often blurred so that only the perpetrators can be identified. “Every face is blurred, except the people that we’re looking for,” Domizio confirmed. “We make it our focus to ensure anonymity. We use a program called Camtasia to edit videos, which lets us blur faces or zoom in on suspects. Any innocent or non-involved person is blurred or edited out of the video.”
All footage posted by police departments comes directly from business and public cameras. “The videos that we post all happen in the public — either in a public place such as a street with outdoor cameras, or in a business where there is surveillance.”
Security cameras with HD resolution noticeably enhance the quality and clarity of the video, making it easier for viewers to discern the scene’s details, including license plate numbers and faces. Day/night cameras that see in extremely low-lit or completely dark environments are beneficial in the evening when crimes generally occur. When businesses invest in these technologies, police will have access to video with greater evidentiary value.
In the end, police realize how crucial it is to make surveillance video available to as many people as possible.YouTube has enabled them to do just that.
 Normally without the use of social media, cartel members stumble across that information by keeping an eye on their surroundings and watching out for flashy individuals. Now, the process is greatly streamlined by having all that information readily available on Facebook. Cartels have been at the cutting edge of this trend. In fact, as early as 2008, Joel Barrios Dueñas noted that instead of waiting for the right person to walk by, the cartel member could sit back, relax, and look through their Facebook Rolodex for the right fit.
Normally without the use of social media, cartel members stumble across that information by keeping an eye on their surroundings and watching out for flashy individuals. Now, the process is greatly streamlined by having all that information readily available on Facebook. Cartels have been at the cutting edge of this trend. In fact, as early as 2008, Joel Barrios Dueñas noted that instead of waiting for the right person to walk by, the cartel member could sit back, relax, and look through their Facebook Rolodex for the right fit.
At that point, the cartel member has the ability to establish a pattern of life, find known associates and images that can help the cartel select and ultimately find the victim, noted Orlando Romero Harrington and Andres Enrique Escoto Castro, in separate pieces on this issue, also back in 2008. Unfortunately, there are many cases that point to the drug cartels’ use of social media for target selection. The most recent and publicized case is the Zetas’ gruesome retaliation against two young men for denouncing their activities on their personal social media accounts, as noted by El Mundo in a 2011 article.
Cartels are also using social media to instill fear in others and deter journalists and private citizens from publishing negative information about the violence they commit. They are using geo-location technology to find computers that have been used to post dialogue that negatively affects their drug trafficking organizations and illicit businesses. For example, there is the documented case of a Mexican blogger who threatened to expose members of a cartel. The cartel responded that 10 people would be killed for every person whose details were leaked. The blogger backed down and chose to sit on the information he claimed to hold.
Cartels are also investing in IT training that would be used to silence Mexican bloggers, such as how to do IP trace routing. They are learning how to tag, track, locate and eliminate people that are blogging the cartel’s activities.
The use of the cloud to perpetrate the Mumbai attacks and the drug cartels’ use of social networking, IP trace routing and geo-tagging to identify victims in the process of target selection are just two examples of force multipliers on the modern battle field. These methods of operation are being used to identify private individuals, corporations, and government entities in ways that are very difficult to defend against. Part of the problem is that it is very difficult for users to implement countermeasures for something that they know little or nothing about, and it is unrealistic to expect people to stop using social media altogether.

